Proxy for Automating: Streamlining Your Workflow
In this swift technological realm, the ability to streamline tasks well can mean the divergence between victory and standstill. For individuals and organizations involved in data harvesting, data extraction, and web research, understanding how to utilize proxies is essential. Proxies can help streamline operations, enhance privacy, and improve connectivity, making them critical tools for simplifying various digital processes.
The following resource will examine the world of proxy services, analyzing the best options for data collection, validating, and verifying proxy lists. If you are looking for a free data scraper or the quickest validation service, we will cover everything you need to know to discover premium proxies and use them successfully for process automation. From the foundations of HTTP and Socket Secure proxies to the nuances of privacy and speed testing, get ready to boost your operations and reveal novel optimizations in your digital activities.
Comprehending Proxies
Proxy servers serve as go-betweens connecting a individual and the internet, allowing users to transmit queries through a external server. When a request is made, it flows through this server, that then forwards the call to the intended website. The website replies to the proxy, that subsequently transmits the information back to the user. This process assists to hide the user's IP address, providing a layer of secrecy and security while browsing or executing scripted actions.
There are numerous types of proxies, such as HTTP and Socket Secure. Hypertext Transfer Protocol proxies are particularly crafted for handling internet traffic, turning them ideal for activities like information harvesting. In opposition, Socket Secure proxies are more versatile, capable of routing any type of data flow, like email and file sharing. Understanding these variances is important for selecting the correct proxy type for particular applications, be it it be SEO tools, data harvesting, or automated workflows.
In furthermore to the types, proxies come in main main categories: dedicated and shared. Private proxies are reserved to individual users, providing greater safety and speed, while shared proxy servers are commonly used among several clients, which can cause reduced speed and higher chances of IP blocking. The decision between private and public proxy servers considerably impacts the success of tasks like web scraping and data collection, underlining the necessity of choosing premium proxies for peak results.
Types of Proxies
Proxies come in many types, each serving distinct purposes based on the needs of users. HTTP proxies are among the widely used, used chiefly for web browsing. They route web traffic through a server, providing features like caching and security. These proxies handle just HTTP requests, which makes them suitable for accessing websites rather than transferring other types of information.
SOCKS proxy servers, on the other hand, are more versatile and can handle all types of traffic, including http, FTP, and more. They can effectively facilitate the transfer of data across different protocols, which makes them suitable for tasks like web scraping and file sharing. SOCKS4 and SOCKS5 are two versions of this type, with the latter offering improved security features like authentication and UDP support, catering to users requiring a more robust solution.
Another type to consider is residential proxy servers, which are Internet Protocol addresses assigned to individuals at home by ISPs. These proxies tend to be more hidden by websites, making them particularly useful for web scraping and scraping data. In contrast, datacenter proxies are generated from data centers and can be less reliable for anonymity. Grasping the distinctions between these types helps in selecting the right proxy for particular automation tasks and streamlining workflows effectively.
Proxy Harvesting Methods
Proxied scraping is an important method for acquiring a list of working proxies that can enhance your information gathering efforts. One of the most efficient approaches involves using a dedicated proxy scraper tool. These tools simplify the task of discovering and gathering proxies from multiple origins across the internet. They can obtain both HTTP and SOCKS servers, often with the choice to sift for anonymity levels. Using a complimentary proxy harvester can be an great initial step, especially for individuals seeking to try the options without any monetary risk. Ensuring that your application is efficient and powerful will preserve you effort and funds.
Another vital element of successful proxy harvesting is the requirement for regular refreshes. Proxies can turn outdated quickly as they may go unavailable or be banned by your desired websites. A recommended strategy is to establish a regular scraping system that refreshes your proxy server list regularly. This can be done through automatic programs or solutions that not only collect new proxy servers but also check their status in live. Integrating a trustworthy proxy validation service ensures that the servers you collect are active and meet your specifications for efficiency and privacy.
Ultimately, comprehending the distinction between different kinds of proxies—namely Hypertext Transfer Protocol, Socket Secure 4, and SOCKS5—will significantly improve your collecting strategy. Hypertext Transfer Protocol servers are typically quicker for standard internet calls, while SOCKS proxies provide a enhanced amount of anonymity and can manage a larger range of traffic types. Knowing when to employ each category will boost your effectiveness plus achievements in web scraping. By using these methods, you can create an improved and successful process for collecting top-notch proxies.
Best Resources for Managing Proxies
Managing proxies efficiently is essential for individuals involved in web scraping or automation tasks. A leading option in this realm is a well-known tool, known for its user-friendly interface and comprehensive features. It simplifies the task of sourcing, verifying, and handling proxy lists. Users like its ability to automate the checking of proxy speed and privacy, making it a must-have tool for professionals looking to enhance their workflow.
Another well-liked option is dedicated proxy scrapers and validators that are designed for particular needs. Tools that focus on complimentary proxies can offer users with a constantly updated list of accessible options. High-speed proxy scrapers are particularly important for users who require fast connections for their automated operations. These tools often come furnished with proxy verification functions, ensuring that you can quickly filter out dead proxies.
Finally, grasping the variations between different proxy types is crucial for efficient management. HTTP proxies are great for web scraping, while SOCKS5 proxies offer greater flexibility and enhanced anonymity. Using a trustworthy proxy list generator online can assist you find the most suitable sources. Coupled with a strong verification tool, these resources enable users to keep a high-quality proxy pool, improving their automation tasks and maximizing overall productivity.
Verifying Proxy Efficacy
Checking the efficacy of proxy connections is important for ensuring that your content harvesting and robotic processes operations run smoothly. A reliable proxy can substantially enhance your capability to browse the web while ensuring confidentiality and circumventing location blocks. Using a dependable proxy checker is the initial step in this procedure, as it allows you to check the performance of a proxy connection, including its latency and anonymity level. how to check if a proxy is working designed for proxy assessment can help identify whether a proxy is functioning correctly and if it fulfills your expectations.
To assess the performance of your proxy connections accurately, execute performance tests that evaluate response time and transfer speeds. Rapid proxy scrapers can automate this task, permitting you to quickly evaluate multiple proxy connections at once. Additionally, comprehending the variations between proxy types, such as HTTP, SOCKS5, is essential, as this can impact your selection and the proxies' effectiveness for targeted tasks. Ensure that the proxy servers you opt for fit your intended use, as various types serve unique functions in data automation.
Finally, it is vital to consistently check your list of proxies for dead or slow proxies, as keeping an up-to-date repository of efficient proxies will boost the overall efficiency of your automated processes. Tools like ProxyStorm and various complimentary proxy scrapers can aid in regularly obtaining efficient proxies while discarding those that do not satisfy your criteria. Checking proxy efficacy ensures that your content harvesting tasks are not obstructed and that you can perform tasks reliably and reliably.
Using Proxies for Automation
Proxy servers play a critical role in streamlining internet tasks, enabling individuals to manage numerous requests without triggering red flags. By directing internet traffic through various proxy servers, you can conceal your IP address and spread requests across varied locations. This is important for web scraping, where frequent and fast requests to the same server can result in short-term or long-term bans. Utilizing a reliable proxy scraper to gather a list of proxies is the initial step in leveraging this power for your automated processes.
Once you have a list of proxies, a reputable proxy checker should be employed to verify their dependability and performance. Not all proxies are the same; some may be sluggish, unreliable, or even dead. Utilizing a proxy verification tool can help evaluate proxy speed, anonymity levels, and types, like HTTPs or SOCKS. This ensures that your automation processes run effectively and efficiently. For more advanced users, methods such as proxy scraping with Python programming can also be incorporated to make the automation process even more advanced.
Finally, grasping the distinction between public and private proxies is essential for automation success. Public proxies are generally complimentary but may suffer from overcrowding and reliability issues, while private proxies offer dedicated resources, boosting speed and security. When building automation systems, evaluate your needs thoughtfully, balancing cost with performance. With the right combination of fast proxy scrapers, efficient proxy checkers, and a strong understanding of proxy types, your automation tasks can become highly effective and successful.
Choosing the Right Proxy for Your Requirements
While picking a proxy for your automated processes, it's important to evaluate the unique demands of your project. For instance, if you're involved in web scraping, you'll want a proxy that can handle large volumes of requests without being denied. In this scenario, using a speedy proxy scraper to gather a comprehensive list of proxies is crucial. Additionally, think about the type of proxy necessary—HTTP proxies may be adequate for simple web browsing, while more advanced tasks might require SOCKS proxies which support a wider range of protocols.
Another important factor is the caliber of the proxies. Premium proxies offer better speeds, lower latencies, and higher anonymity levels. You can employ a proxy verification tool or the most effective proxy checker to evaluate the performance of the proxies you've gathered. Be sure to investigate options like free proxy scrapers and their restrictions versus paid solutions, which often provide access to more reliable and more efficient proxies, guaranteeing that your workflow remains seamless.
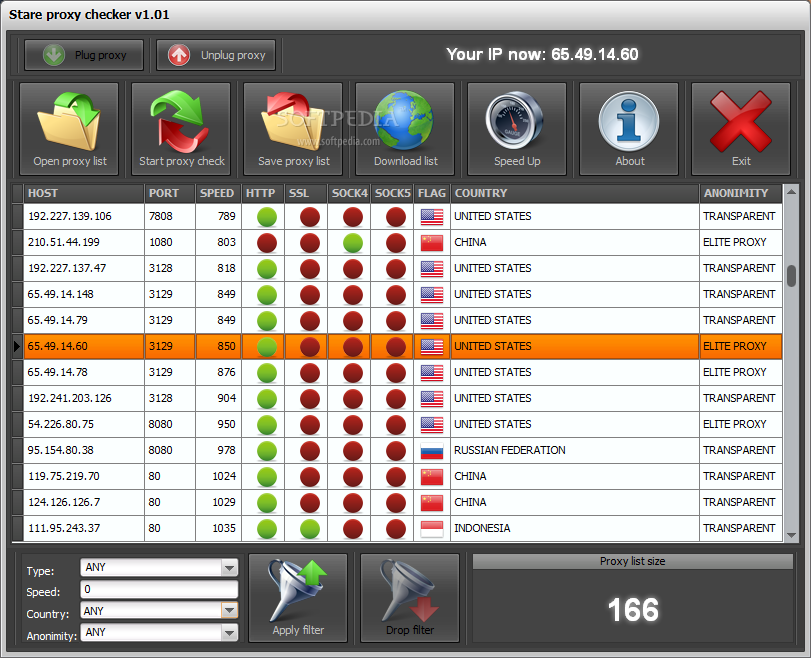
Finally, always assess the providers of your proxies. The most effective proxy sources for web scraping can provide lists of proxies that are consistently maintained and vetted for performance. Whether you choose private or shared proxies, comprehending the difference in their use cases is vital. Incorporating efficient proxy management strategies and tools will assist improve your workflow, ultimately enhancing your productivity and efficiency in automation activities.